![]()
Almost two months after releasing details of 23 different secret CIA hacking tool projects under Vault 7 series, Wikileaks today announced a new Vault 8 series that will reveal source codes and information about the backend infrastructure developed by the CIA hackers.
Not just announcement, but the whistleblower organisation has also published its first batch of Vault 8 leak, releasing source code and development logs of Project Hive—a significant backend component the agency used to remotely control its malware covertly.
In April this year, WikiLeaks disclosed a brief information about Project Hive, revealing that the project is an advanced command-and-control server (malware control system) that communicates with malware to send commands to execute specific tasks on the targets and receive exfiltrated information from the target machines.
Hive is a multi-user all-in-one system that can be used by multiple CIA operators to remotely control multiple malware implants used in different operations.
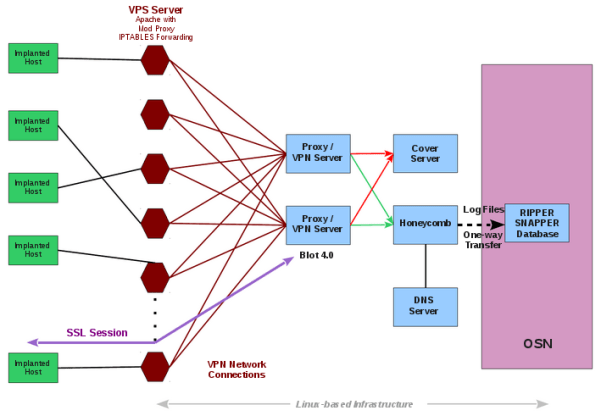
Hive’s infrastructure has been specially designed to prevent attribution, which includes a public facing fake website following multi-stage communication over a Virtual Private Network (VPN).
“Using Hive even if an implant is discovered on a target computer, attributing it to the CIA is difficult by just looking at the communication of the malware with other servers on the internet,” WikiLeaks says.
As shown in the diagram, the malware implants directly communicate with a fake website, running over commercial VPS (Virtual Private Server), which looks innocent when opened directly into the web browser.
However, in the background, after authentication, the malware implant can communicate with the web server (hosting fake website), which then forwards malware-related traffic to a “hidden” CIA server called ‘Blot’ over a secure VPN connection.
The Blot server then forwards the traffic to an implant operator management gateway called ‘Honeycomb.’
In order to evade detection by the network administrators, the malware implants use fake digital certificates for Kaspersky Lab.
“Digital certificates for the authentication of implants are generated by the CIA impersonating existing entities,” WikiLeaks says.
“The three examples included in the source code build a fake certificate for the anti-virus company Kaspersky Laboratory, Moscow pretending to be signed by Thawte Premium Server CA, Cape Town.”
The whistleblowing organisation has released the source code for Project Hive which is now available for anyone, including investigative journalists and forensic experts, to download and dig into its functionalities.
The source code published in the Vault 8 series only contains software designed to run on servers controlled by the CIA, while WikiLeaks assures that the organisation will not release any zero-day or similar security vulnerabilities which could be abused by others.
from : Thehackernews Thursday, November 09, 2017
link : https://thehackernews.com/2017/11/cia-hive-malware-code.html